This particular Negative SEO tactic is one of the most common, but also most effective. In this post we’ll walk you through the steps involved and the countermeasures you’re able to take if a jealous competitor, disgruntled ex-employee, or a “bad actor for hire” launches this type of attack on your website.
If carried out properly and persistently, a Link Removal attack can have devastating consequences on the target website’s ranking, though this will take some time and effort on the part of the attacker.
Breakdown of a Link Removal Request Attack:
Step #1: Impersonation
The main aspect behind a successful Link Removal Attack is for the attacker to make his/her email link removal requests look as authentic as possible. The more the outreach email looks as though it’s actually coming from your target’s own company, the greater your chance of its recipient acting on it and removing the link[s] to the attacker’s target’s website.
Step #2: List Building
The next step is to compile a list of the most valuable links to the victim’s website. This can be accomplished by using either a paid-for or a free “Backlink Checker Tool.” Once the attacker has built his/her list, they need to obtain technical contact information for each site, so as to have a means of requesting for the desired link[s] to be removed. This is usually the most time-consuming aspect of the Link Removal Request NSEO Attack Vector.
Step #3: Making Link Removal Requests
Once the link and contact lists are complete, the attacker begins to send very authentic appearing link removal requests to the contacts on his or her list. The more authentic the look and tone of these, the greater the chance of the recipient acting on it.
NOTE: There are of course far more details and sub-steps involved in this attack vector. These are beyond the scope of this article, because this site is designed as a way to raise awareness about Negative SEO, not as a “How-To” instruction manual for unethical SEOs and other bad actors.
How to Defend Your Website Against a Link Removal Request Attack:
The Bad News is that there is no defense available against this type of NSEO attack.
The Good News is that with proper monitoring of your website’s link profile you’re able to set up an “early warning system” that alerts you of unusual and/or nefarious activity in your website’s backlink profile.
This can most easily be accomplished by using the tools available at Majestic.com¹, which is ArcLite’s weapon of choice for Backlink Analysis, Link Penalty Recovery, and Inbound Link Audits.
Using Majestic’s “Lost Links” graph, it’s easy to keep track of any unusual patterns in your website’s inbound link profile, since it tracks link-loss on a daily basis, and provides you with an easy overview of each link’s value via its TrustFlow/CitationFlow matrices.
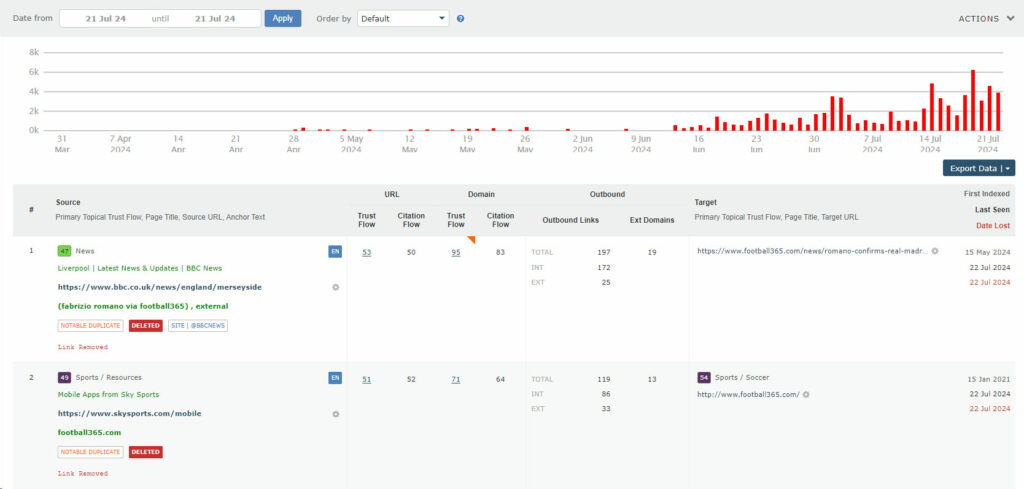
Once you identify a Link Removal Attack against your site, you’re able to undo the damage by contacting the websites which removed links to you, explaining the situation and asking them to reinstate “the “lost” link[s].
Caught early on, the damage caused by this Negative SEO attack vector is minimal. If left to develop unchallenged for an extended period, however, the negative ranking consequences can be considerable or even catastrophic.
Pro-Tip: Keeping a list of contact details for the websites containing your most valuable inbound links can save a lot of time in case of a concerted Link Removal campaign against you.
You won’t need to worry about your entire link profile, but if you take the time to compile such a contact list for the top 50 or top 100 links to your site, you’ll be able to act more or less instantly, the moment you identify the negative pattern.
¹ And no, Majestic still isn’t paying us to say any of this. We use their tools because they’re superior…

